Intune setup
Depending on what you want to archieve with client certificates there's a few typical steps you want to do.
- Deploy your EasyScep Root Certificate as a trusted CA
- Deploy one or more certificates to your devices for client authentication
- Deploy network connectivity profiles like Wi-Fi, LAN and VPN.
You can see the detailed instructions in this document for each of the use cases.
Documentation here is primarily for Windows 10/11 profiles, but it's almost identical for other platforms.
Configuring Intune
Prerequisites
To start deploying certificates using Microsoft Intune, be sure to check that your EasyScep instance is configured correctly. Check our on-boarding guide here if you have not yet done so yet.
Creating the Root Certificate Trust
First, you need to upload the certificate into Intune and register as trusted.
Note: you should create a trusted profile for every platform you are using.
-
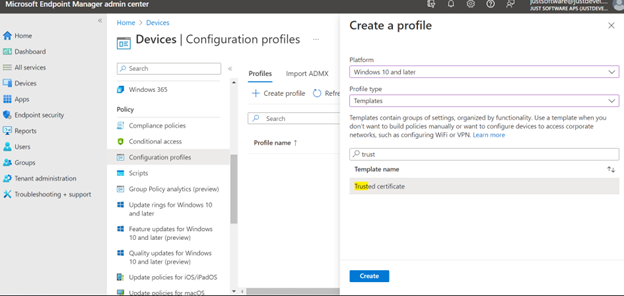
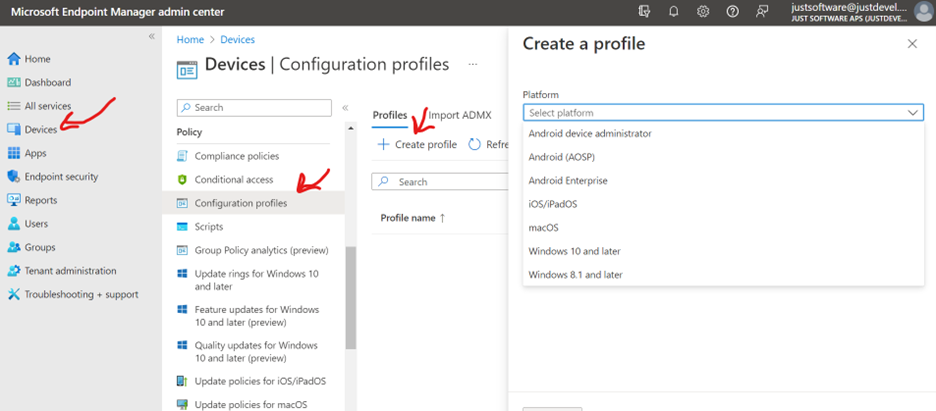
Go to https://endpoint.microsoft.com/ > Devices > Configuration profiles and click on “Create profile”.
-
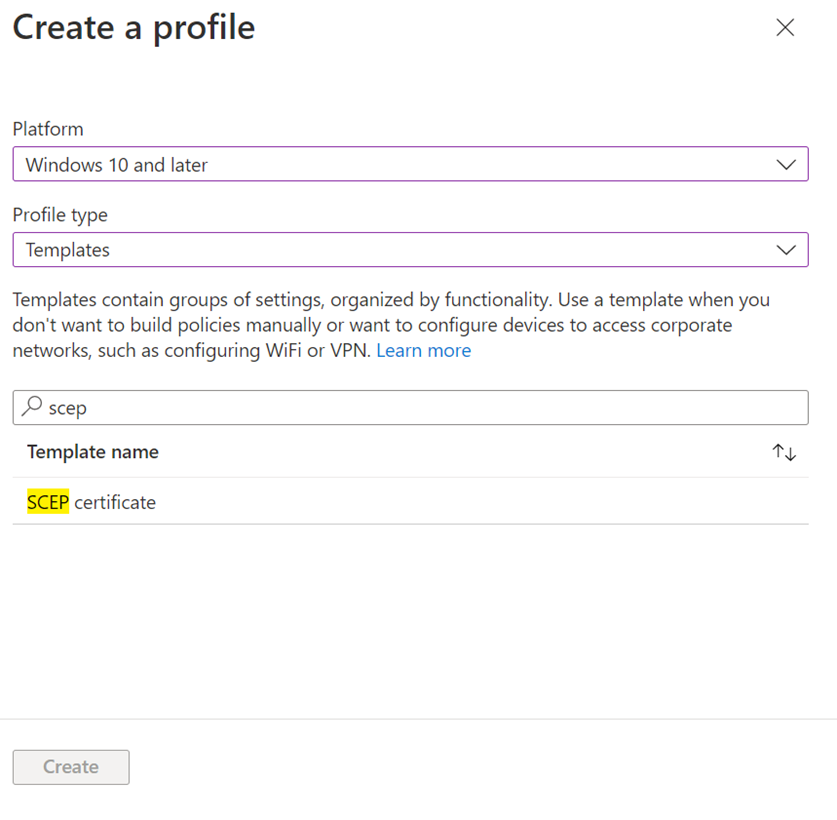
On “Create profile” page choose the needed platform. In Profile type select “Templates” and in Template name find “Trusted certificate” and click on “Create”
-
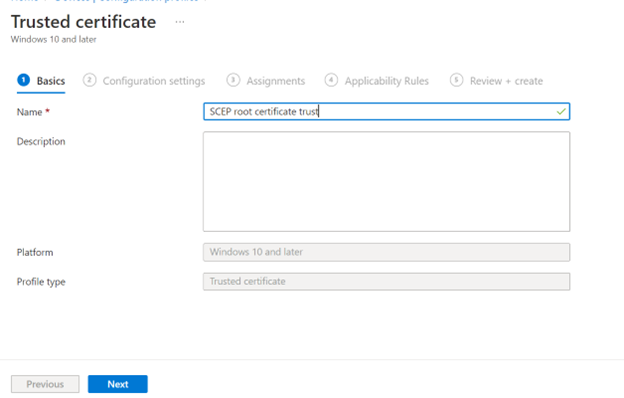
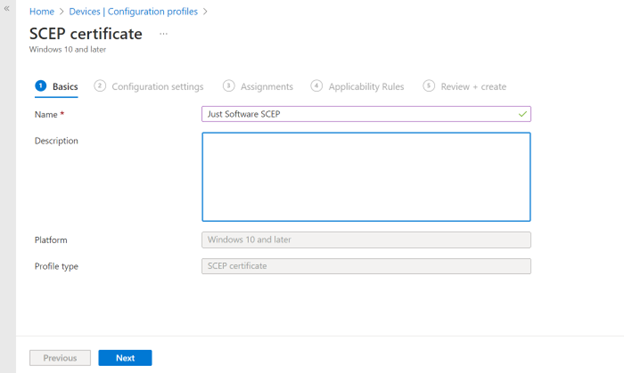
Fill in a name for the trusted certificate profile
-
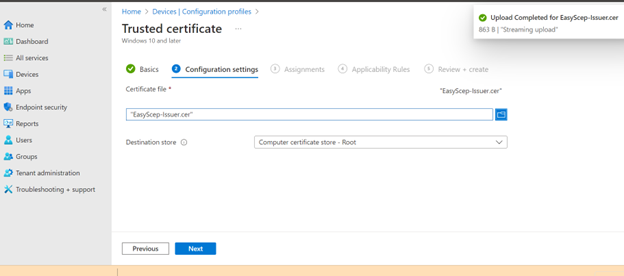
Upload certificate which is downloaded from the EasyScep administration portal.
-
Choose deployment scope, this is often "All users" or "All devices" for a Certificate Authority trust.
Adjust according to your requirements.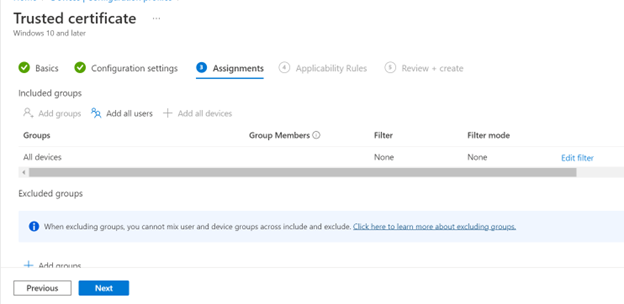
-
Click on “Next” until to get to the last page, where you click on “Create” to save your profile.
Issuing client certificates
- Go to Intune administration page https://endpoint.microsoft.com/ > Devices > Configuration profiles
-
Click on Create profile
-
On the Create profile page, choose Template -> SCEP Certificate.
-
Name your SCEP Profile
-
On the Configuration settings tab choose:
| Setting | Value |
|---|---|
| Certificate type | User or Device, for VPN and WiFi usage, device certificates is recommended |
| Subject name format | e.g. "CN={{UserName}},E={{EmailAddress}}" |
| Certificate type | Device |
 For most cases (e.g. WiFi / network access), device certificates are recommended. For most cases (e.g. WiFi / network access), device certificates are recommended. |
|
| Subject name format | CN={{AAD_Device_ID}},OU=Windows,OU=Devices,O=MyOrg Inc,C=US |
| Certificate validity period | 3 months (you can make it 1 month, 1 day, etc. This is a certificate that is issued to the client.) |
 Typical anywhere between 3 months and 1 year. Typical anywhere between 3 months and 1 year. |
|
| Key storage provider (KSP) | Enroll to Trusted Platform Module (TPM) KSP if present, otherwise Software KSP |
 It's recommended to use Software storage on windows for initial testing and deployment since faulty TPM's are often seens and causes hard to troubleshoot errors. It's recommended to use Software storage on windows for initial testing and deployment since faulty TPM's are often seens and causes hard to troubleshoot errors. |
|
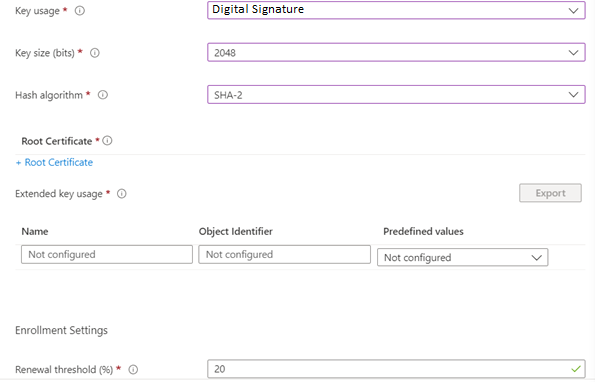
| Key usage | Digital Signature |
| Key size (bits) | 2048 (recommended) |
| Hash algorithm | SHA-2 |
| Root Certificate | choose the one added on trusted certificate (in this example it is “SCEP root certificate trust”) |
| Extended key usage | Choose in Predefined values “Client Authentication (1.3.6.1.5.5.7.3.2)” |
| SCEP Server URLs | you can find the link(s) in the EasyScep administration portal |

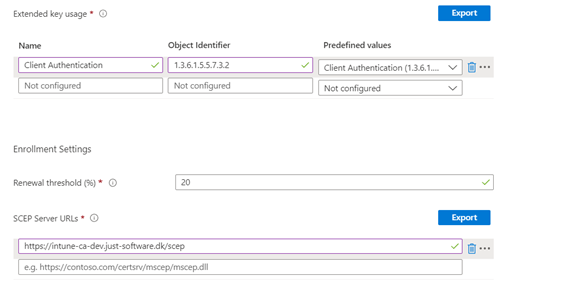
-
On The Assignments tab ensure you assign the devices which should receive certificates by using a filtered group which contains the users and/or devices you want to deploy SCEP certificates for.
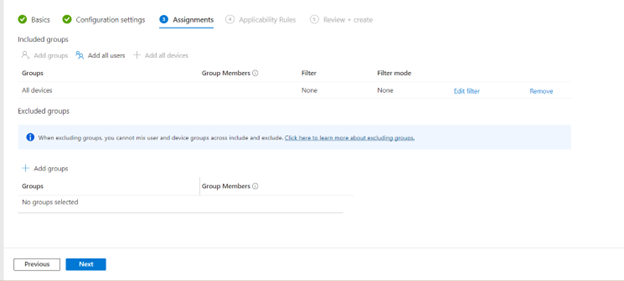
-
Save your profile and validate that it works by forcing sync on a client